Last week at Open Mainframe Summit, hosted on September 21-22 in Philadelphia, PA and virtually, David Wheeler, the Open Source Director of Security Supply Chain at the Linux Foundation, presented a keynote about how to evaluate OSS security before incorporating it, activities you can do to improve your security and the Open Source Security Foundation (OpenSSF).
Security is not new in the mainframe world, but it continues to become a larger concern across all of IT. Here are some mainframe folks’ main concerns about security:
- Reliability and availability concerns (RAAS)
- Porting concerns with big-endian
The implications of this are:
- Buffer overflows are a serious vulnerability in most of the industry. And it has caused severe recommendations, such as turning off key features just to avoid it.
- Vulnerable dependency software within the mainframe can infect your code, e.g. Log4shell and Log4j.
Attacks on the Software Supply Chain
Attacks on the software that many mainframe applications depend on are growing. This growth is close to exponential. This is something we need to pay attention to, from industry to government action. And it’s happening—consider the executive order for national cybersecurity, which attempts to review these attacks and give recommendations.
The most common type of supply chain attack is package name typosquatting. This is a somewhat fancy way of saying attackers create malicious variants of projects/packages with typos in the names, like L0g4shell instead of Log4shell.
Another kind of attack is dependency confusion. This is where an attacker makes a public version of an internal package your software uses. So the package managers will go grab the version from the public repository instead of your organization’s internal one. This is a new attack, which became popular in 2021. The irony of this attack is that companies thought creating internal repositories would make things more secure, when in fact, if used wrongly, it can make things worse!
This all leads to a more general problem: most projects and organizations don’t know the entirety of the software that is running on their systems!There is no clear, consistent, and easy way to summarize and publish it.
Solutions
The OpenSS Foundation was constructed to help solve this. Its structure is similar to the Linux Foundation: it’s a committee with proposals that get approved. One of the things recently released is a concise guide for developing more secure software.
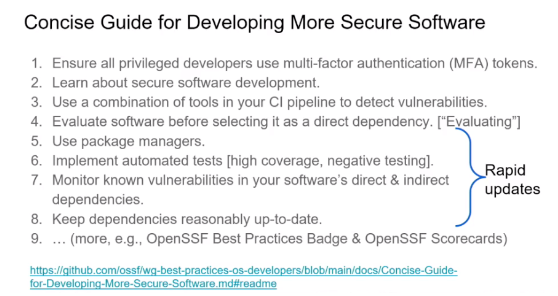
This guide includes key practices that we have seen become more popular, such as using multi-factor authentication, ensuring your developers are security-trained, and using vulnerability detection in your CI pipeline.

A key here is that a team needs to be prepared to do rapid updates in order to plug security holes as quickly as possible. The impact of a security vulnerability can exponentially grow based on the rate it is exposed. Half of OpenSSF’s concise guide focuses on this.
One of the guide’s main points is evaluating OSS. But how exactly do we do this? OpenSSF has some recommendations. For instance, consider avoiding adding the OSS package. Sometimes we take dependencies for simple logic we can implement ourselves. You also want to review an open source package’s dependencies to understand how much is built into it. Check if they have a “security checklist” or a security guide.
You can even automate some of the evaluation, such as via the OpenSSF Scorecards. If you own an OSS project, you can make it easier for developers to evaluate your security through things like coordinated vulnerability disclosure. This may even be the #1 most common missing item when starting an OSS project.
Conclusion
If you are interested in OSS security, please get involved. Historically, we assumed organizations releasing software were keeping it up to date. Turns out that it’s a terrible assumption. Ensure your developers are trained and put tools and processes in place to review not only your software but your supply chain: the software you depend on. You can also join numerous OSS projects, like OpenSSF, that combat supply chain attacks.
Registrants of Open Mainframe Summit have access to all of the keynote presentations and sessions. If you did not register or attend the event, Open Mainframe Project will make the videos available on our Youtube Channel in the next few weeks. Until then, if you have questions about the event, security or any of the Open Mainframe Project, join the community on Slack.